The automotive sector has transformed into one of the most promising digital industries in the world. Cars are not only mechanical assets, but they are rolling computers with software, connectivity, and data flowing in real-time. In addition, dealer networks have moved from paper files and basic billing systems to cloud-based CRMs, online booking, connected diagnostics, and integrated automotive DMS software.
So, in this environment, automotive cyber security is not just about securing vehicles or factory systems. But it also focuses on ensuring every point where data is created, viewed, or modified across the ecosystem. Well, this includes the dealerships, which are one of the busiest and most exposed digital touchpoints in the entire network.
Still, in most cases, dealership systems don’t receive the same level of security as other OEM data centres.
OEMs often assume, “we protect our data; dealers will secure theirs.” But their systems are very tightly connected, and this means that a dealer’s weak spot becomes an OEM’s weak spot. Therefore, modern automotive cybersecurity should treat every dealership not as a separate business, but as an essential segment in one shared data network.
Why Automotive Cyber Security Needs a Different Approach
Vehicles run on software, manufacturing runs on cloud systems, and dealerships run on integrated automotive DMS software platforms that communicate with OEM servers in real time. This means that cyber security in automotive industry is no longer just restricted to protecting factories or in-vehicle electronics. It should also extend across every node, every dealership, every user, and every system that participates in the OEM’s data ecosystem.
To add to this, dealerships have transitioned from paper-based outlets to digital command centres that is responsible for looking after the sensitive information that requires strong OEM cyber security controls.
Dealerships help in processing customer identities, finance approvals, test-drive requests, service data, job cards, warranty claims, and inventory management and much of these functions through OEM-linked platforms. Due to all this, cyber-attacks on automotive industry networks primarily focus on dealerships that often have weaker defences.
Therefore, to stay protected, OEMs must treat every dealership as an essential part of the data node in the network that is fully aligned with automotive cyber security, automotive cyber security standards, and modern OEM cyber security practices.
Why Traditional Automotive Cybersecurity Isn’t Enough
Traditional cyber security in automotive industry was designed to cater to a different era, that is, one where the majority of the data rested inside the OEM’s walls. But today, the data is scattered across hundreds of dealer outlets, thousands of devices, and dozens of integrated systems.
This expanded environment means that the older security models cannot keep up, especially when modern cyber-attacks on automotive industry systems target the weakest endpoints.
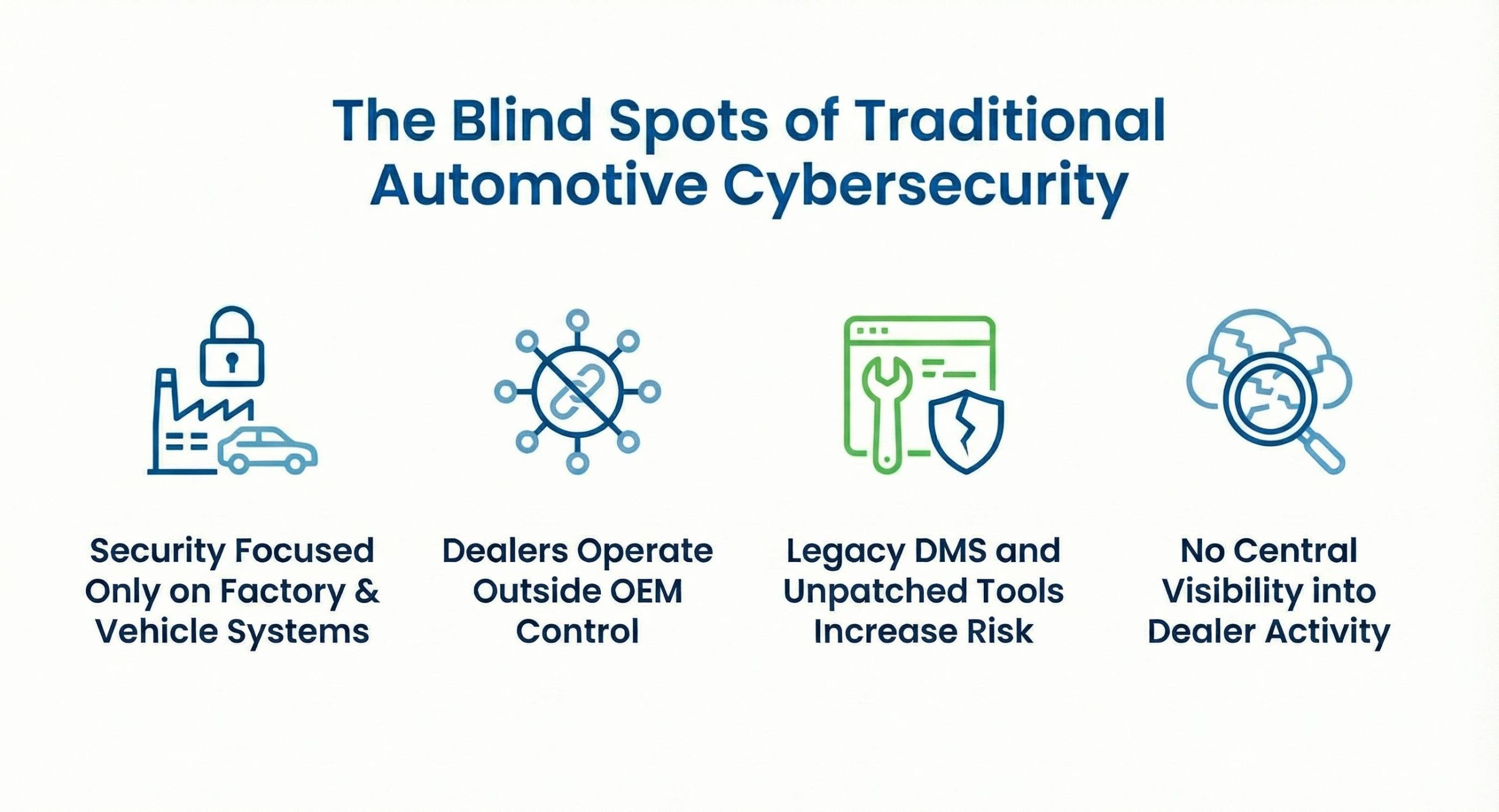
Mentioned below are the disadvantages of traditional approaches:
- Security Focused Only on Factory & Vehicle Systems
- Dealers Operate Outside OEM Control
- Legacy DMS and Unpatched Tools Increase Risk
- No Central Visibility into Dealer Activity
OEMs secured ECUs, production lines, and internal networks, but dealer systems never got the same OEM cyber security attention. Dealers handle sensitive customer and financial data, making them easy targets. If a dealer is breached, OEM-linked APIs and portals are exposed—showing why automotive cyber security must cover dealerships too.
Dealers have their own budgets, tools, and IT rules, causing uneven cyber security OEM practices. Some follow strong protocols, others don’t. Attackers exploit the weakest link to enter the OEM network. Without shared automotive cyber security standards, the entire ecosystem stays at risk.
Many dealers still use outdated automotive DMS software and old hardware that lack updates. These gaps allow ransomware or unauthorised access that can travel through OEM integrations. Strong automotive software security governance is now essential.
Traditional cyber security in automotive industry models doesn’t account for the many dealer endpoints OEMs can’t see. Without visibility into dealer logins and data use, threats go undetected. Wide-network monitoring is now a core need in automotive cyber security.
How Connected Dealer Networks Increase Cyber Risks
Connected systems streamline work, but they also tend to create new attack pathways that did not exist a while ago. Every API, login, diagnostic device, and service portal expands the attack surface of the vehicle’s ecosystem thereby emphasising on the need to provide strong automotive cyber security at every layer.
- Dealers Use Multiple Integrated Systems Daily
- Large Amounts of Customer Data Flow Through Dealers
- Ransomware Can Shut Down Dealer Operations Completely
- Attackers Can Manipulate OEM–Dealer Data Exchange
Dealers work with CRMs, DMS platforms, diagnostic apps, OEM portals, parts ordering tools, and finance systems. All these integrations should be able to meet automotive cyber security standards, or attackers can easily intercept data. The more systems a dealer connects, the more important strong OEM cyber security becomes.
Dealers handle Aadhaar, PAN, bank details, loan forms, signatures, and addresses—making them major targets for identity theft and fraud. Without proper automotive cyber security, a single breach can expose thousands of records and harm dealer and OEM reputation.
Weak endpoints leave dealers open to ransomware that can freeze their DMS, billing tools, or service apps. Most of them still use outdated automotive DMS software, making attacks easier. When systems lock, job cards, invoices, and service flow stop—creating delays, customer frustration, and lost revenue for OEMs.
Dealers upload warranty claims, inventory orders, and service updates to OEM platforms. If attackers access a dealer login, they can send fake claims or alter records. Strong cyber security OEM frameworks are needed to prevent manipulation of these shared systems.
Core Security Areas OEMs Must Strengthen
To treat dealers like data networks, OEMs should focus on securing and strengthening four pillars that are: data protection, integration security, software security, and monitoring. These pillars are the heart and soul of modern automotive cyber security standards used by leading OEMs.
- Data Protection & Privacy Controls
- Securing OEM–Dealer Integrations
- Automotive Software Security
- Real-Time Monitoring & Threat Detection
Dealerships handle extremely sensitive customer data. If stored casually or shared insecurely, this information becomes easy to steal—making strong automotive cyber security practices essential.
OEM–dealer communication is heavily dependent on secure APIs and data pipelines. So, these must comply with automotive cyber security standards to ensure attackers cannot manipulate vehicle, service, or warranty data.
Dealers use diagnostic tools, local applications, mobile apps, and DMS systems across multiple devices. Unpatched software can become a gateway for attackers—making automotive software security vital for both OEM and dealer safety.
OEMs must detect suspicious login patterns, abnormal data usage, and potential breaches in real time. This aligns with modern cyber security in automotive industry requirements, where continuous monitoring is now considered mandatory.
Common Cybersecurity Gaps in Dealer Networks
Dealer networks remain one of the weakest links in the automotive cyber security chain. Most dealerships function with limited IT support, uneven security practices, and outdated systems—creating easy entry points for attackers. When these vulnerabilities go unchecked, they expose the entire OEM ecosystem to major data and operational risks.
- Dealer Vulnerabilities Spread into OEM Systems
- Local Storage of Sensitive Customer Data
- Lack of Unified Automotive Cyber Security Standards
If even one dealer workstation gets infected with malware, the threat can move upward through DMS–OEM integrations, APIs, diagnostic tools, or portals. Modern cyber security in automotive industry practices highlight this exact pattern, which is why securing dealer endpoints is now critical.
Many dealers store Aadhaar cards, PAN numbers, bank documents, loan forms, and signatures on local systems. This exposes OEMs to compliance and privacy risks because customer data is not sufficiently protected.
Because each dealer uses different tools, policies, and processes, cybersecurity varies widely across the network. Without consistent automotive cyber security standards, OEMs cannot ensure full data protection or defend their ecosystem against coordinated attacks.
How OEMs Can Build a Strong Cyber Defense
It is important for the OEMs to implement network-wide cybersecurity which means extending standards, monitoring, and technology across their dealer ecosystem.
- Unified Cybersecurity Policy
- Secure Cloud-Based DMS
- Identity & Access Controls
- Dealer Training
OEMs should define clear rules for passwords, software usage, data handling, and reporting. These guidelines help enforce consistent automotive cyber security behaviors across outlets.
Legacy DMS installations are a major risk. Modern systems like NetFlows360 reduce exposure by providing secure, cloud-native automotive DMS software that updates automatically.
Dealers must use restricted access and multi-factor authentication. Weak credentials are one of the leading causes of cyber attacks on automotive industry.
Human error causes most breaches. Training ensures staff can recognize scams, protect customer data, and follow automotive cyber security best practices.
NetFlows360: A Safer Digital Path for OEM–Dealer Ecosystems
NetFlows360 strengthens cybersecurity across the entire OEM–dealer ecosystem by offering secure integrations, encrypted data flows, and protected user access.
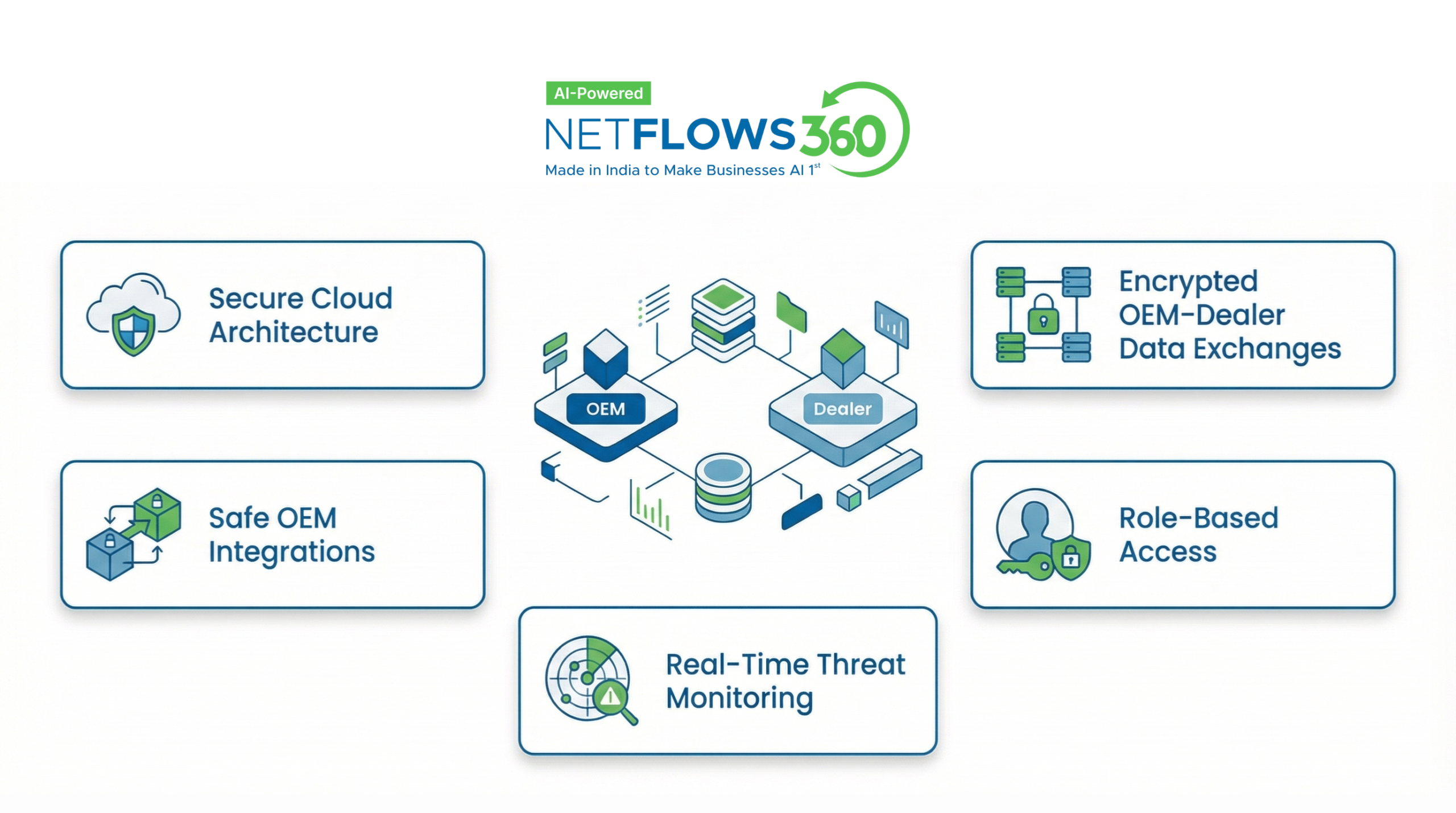
- Secure Cloud Architecture
- Encrypted OEM–Dealer Data Exchanges
- Role-Based Access
- Safe OEM Integrations
- Real-Time Threat Monitoring
Dealers always operate on the safest version of the system. This architecture reduces vulnerabilities commonly found in older automotive DMS software.
Sensitive information—like customer profiles, loan data, and service records—always travels through encrypted channels, strengthening automotive cyber security.
Users receive only the permissions they need. This protects OEM systems from unauthorised dealer access attempts.
NetFlows360 uses secure APIs built to support advanced automotive software security requirements, minimising integration risks.
Suspicious login activity, data downloads, and service anomalies are flagged instantly thereby enhancing overall cyber security OEM oversight.
Wrap Up
Modern dealer networks act as digital extensions of OEMs. This means cyber security must flow across the ecosystem—not stop at the manufacturer’s boundary. When OEMs secure dealers with consistent standards, encrypted systems, and centralised monitoring, the entire network becomes more resilient.
As cyber threats continue to rise, adopting strong automotive cyber security strategies with solutions like NetFlows360 is no longer optional—it is essential for protecting customers, dealers, and OEM brand trust.
FAQs
It refers to the protection of connected vehicles, OEM systems, dealer networks, and customer data from digital threats.
They run multiple digital systems, making them easier to break into compared to OEM data centres.
A breach at the dealer level can manipulate inventory, warranty, and customer data—impacting the OEM directly.
It provides encrypted communication, secure access controls, and integrated monitoring aligned with automotive cyber security standards.